| < Previous by Date | Date Index | Next by Date > |
| < Previous in Thread | Thread Index | Next in Thread > |
Re: [reSIProcate-users] TLS Handshake failure on debian 8
- From: Florent SCHILDKNECHT <florent.schildknecht@xxxxxxxxx>
- Date: Mon, 30 Jan 2017 18:14:39 +0100
Hey Scott, Thanks for your reply, I’ll try to answer as best as I can. Not sure if it matters, but I am wish to use this TURN server as a relay for a WebRTC application. I already have working JS clients and a signaling server. To test my turn server, I use this tool : I first set the 3478, unencrypted address, then I try using the port 5349, which is my TlsTurnPort. First test (port 3478, seems to work) : URL : turn:turn.my-domain.com:3478 username : test credential : « my-hashed-password » Time Component Type Foundation Protocol Address Port Priority 0.002 1 host 1026183099 udp My_Local_IP 51014 126 | 32542 | 255 0.002 2 host 1026183099 udp My_Local_IP 59034 126 | 32542 | 254 0.044 1 srflx 3160557839 udp My_Public_IP 34652 100 | 32542 | 255 0.049 2 srflx 3160557839 udp My_Public_IP 34653 100 | 32542 | 254 0.102 1 host 1940501323 tcp My_Local_IP 9 90 | 32542 | 255 0.102 2 host 1940501323 tcp My_Local_IP 9 90 | 32542 | 254 0.165 1 relay 4193894297 udp My_Server_IP 49156 2 | 32542 | 255 0.168 2 relay 4193894297 udp My_Server_IP 49157 2 | 32542 | 254 0.169 Done Second test (port 5349) : Time Component Type Foundation Protocol Address Port Priority 0.002 1 host 1026183099 udp My_Local_IP 58981 126 | 32542 | 255 0.002 2 host 1026183099 udp My_Local_IP 58354 126 | 32542 | 254 0.103 1 host 1940501323 tcp My_Local_IP 9 90 | 32542 | 255 0.103 2 host 1940501323 tcp My_Local_IP 9 90 | 32542 | 254 9.560 Not reachable? 1. I’ve set the logger level to DEBUG in the reTurnServer.config file. Now, I have those logs : ## Server start INFO | 20170130-171540.513 | reTurnServer | RETURN | 140023855642432 | UdpServer.cxx:30 | UdpServer started. Listening on X.X.X.X:3478 INFO | 20170130-171540.513 | reTurnServer | RETURN | 140023855642432 | TcpServer.cxx:35 | TcpServer started. Listening on X.X.X.X:3478 INFO | 20170130-171540.515 | reTurnServer | RETURN | 140023855642432 | TlsServer.cxx:73 | TlsServer started. Listening on X.X.X.X:5349 INFO | 20170130-171540.515 | reTurnServer | RETURN | 140023855642432 | UdpServer.cxx:30 | UdpServer started. Listening on Y:Y:Y:Y:Y:Y:3478 INFO | 20170130-171540.515 | reTurnServer | RETURN | 140023855642432 | TcpServer.cxx:35 | TcpServer started. Listening on Y:Y:Y:Y:Y:Y:3478 INFO | 20170130-171540.516 | reTurnServer | RETURN | 140023855642432 | TlsServer.cxx:73 | TlsServer started. Listening on Y:Y:Y:Y:Y:Y:5349 ## When I try to connect my webrtc DEBUG | 20170130-173043.614 | reTurnServer | RETURN | 140023809464064 | TlsConnection.cxx:44 | TlsConnection started. WARNING | 20170130-173047.462 | reTurnServer | RETURN | 140023809464064 | TlsConnection.cxx:80 | TlsConnection handshake failure, error=336130315-wrong version number DEBUG | 20170130-173047.462 | reTurnServer | RETURN | 140023809464064 | TlsConnection.cxx:32 | TlsConnection destroyed. The openssl version I am using is : OpenSSL 1.0.1t 3 May 2016 2. Not exactly sure of what you mean by « installed » ; I am using letsencrypt, so unless I really get something wrong, The root CA is the one of LetsEncrypt, which usually does not need any installation ? Here is a screen of the certificate when I access the domain on port 443 (Using nginx, no web-application of any kind on this domain though) 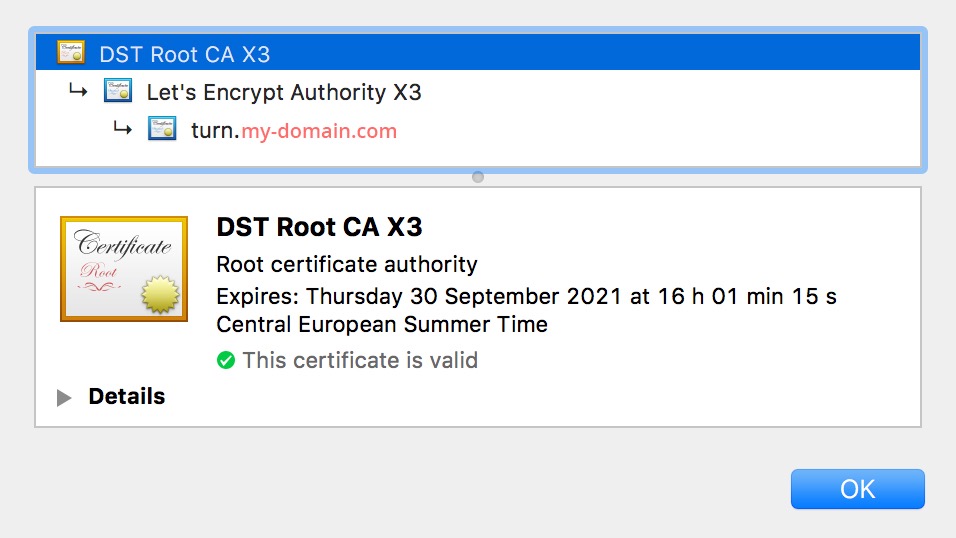 (Which means the certificate is valid... Right?) 3. I really think so, even though I am using the webrtc.github.io tool, The URL that is set is indeed turn.my-domain.com, which is the Common Name of my certificate. 4. I have never used wireshark, so it’s not easy to understand how it works, but I gave it a try. Not actually sure what kind of information I am looking for? Here is a screen of some frames that I could consider related, given the fact that it is the good server IP address… 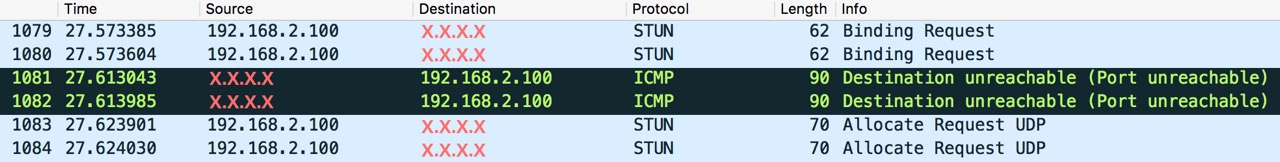 Thanks again in advance, Best regards, Florent Schildknecht UX-designer et développeur web auto-entrepreneur +33 6 78 41 74 79 (France)+46 7 64 15 32 64 (Sweden)
|
Attachment:
signature.asc
Description: Message signed with OpenPGP using GPGMail
- Follow-Ups:
- Re: [reSIProcate-users] TLS Handshake failure on debian 8
- From: Scott Godin
- Re: [reSIProcate-users] TLS Handshake failure on debian 8
- References:
- [reSIProcate-users] TLS Handshake failure on debian 8
- From: Florent SCHILDKNECHT
- Re: [reSIProcate-users] TLS Handshake failure on debian 8
- From: Scott Godin
- [reSIProcate-users] TLS Handshake failure on debian 8
- Prev by Date: Re: [reSIProcate-users] TLS Handshake failure on debian 8
- Next by Date: Re: [reSIProcate-users] TLS Handshake failure on debian 8
- Previous by thread: Re: [reSIProcate-users] TLS Handshake failure on debian 8
- Next by thread: Re: [reSIProcate-users] TLS Handshake failure on debian 8
- Index(es):